
Cloud Security Posture Management (CSPM)
SAAS based service which identifies risks, misconfigurations, vulnerabilities, detects threat also provides remediation workflows to fix misconfiguration across multi-cloud environment. The CSPM applies common frameworks, regulatory compliance and enterprise policies to proactively and reactively discover and assess risk of cloud services configuration and security settings. CSPM tools offers automated remediation playbooks if any issues are identified based on policies configured.
While cloud providers offer some basic risk assessment and configuration, CSPM delivers both more advanced controls and multi-cloud capabilities. Through security assessments and automated compliance monitoring. The cloud security shared responsibility model divides security and compliance responsibilities between the cloud service provider (CSP) and the customer. And this model's specifics may vary depending on the cloud service model in use, such as infrastructure as a service (IaaS), platform as a service (PaaS), or software as a service (SaaS)
Cloud hosting provider is not responsible for security and if an enterprise assumes that CSP will provide security and don’t add cloud security measures then this leads to data breaches and other security issues. Cloud security posture management (CSPM) consists of offerings that continuously manage IaaS and PaaS security posture through prevention, detection and response to cloud infrastructure risks.
Cloud Security Posture Management (CSPM)
is asset of tools designed to ensure security compliance and best practices across cloud infrastructure. Here are the key subcomponents of CSPM
Configuration Management
- Configuration Monitoring: Continuously monitoring cloud resources for configuration changes that could introduce security risks.
- Baseline Configuration: Establishing and maintaining secure baseline configurations for cloud resources.
- Drift Detection: Identifying deviations from the baseline configuration to detect unauthorized changes.
Compliance Management
- Policy Enforcement: Applying and enforcing security policies across cloud environments to ensure compliance with standards and regulations.
- Audit and Reporting: Generating reports demonstrating compliance with industry standards (e.g., GDPR, HIPAA, PCI-DSS).
- Regulatory Mapping: Mapping cloud configurations and policies to specific regulatory requirements.
Risk Assessment
- Risk Identification: Identifying potential security risks in the cloud infrastructure.
- Risk Scoring: Assigning risk scores to cloud assets based on their configuration and exposure to threats.
- Prioritization: Prioritizing remediation actions based on the risk scores and impact on the organization.
Threat Detection
- Anomaly Detection: Detecting unusual patterns or behaviours that may indicate security threats.
- Threat Intelligence Integration: Incorporating threat intelligence feeds to stay updated on the latest threats and vulnerabilities.
- Alerting: Generating alerts for suspicious activities or configurations that could pose security risks.
Automation and Orchestration
- Automated Remediation: Automatically fixing identified issues and misconfigurations.
- Workflow Automation: Automating workflows for incident response and compliance checks.
- Integration with DevOps: Integrating CSPM tools with DevOps pipelines to ensure security throughout the development lifecycle.
Visibility and Monitoring
- Asset Inventory: Maintaining an up-to-date inventory of all cloud assets, including compute, storage, and network resources.
- Resource Tagging: Tagging resources to organize and manage them effectively.
- Real-Time Monitoring: Providing real-time visibility into the security posture of cloud environments.
Identity and Access Management (IAM)
- IAM Policy Monitoring: Monitoring and analysing IAM policies to ensure they follow the principle of least privilege.
- User Activity Monitoring: Tracking user activities to detect any unauthorized or suspicious behaviour.
- Access Reviews: Conducting regular reviews of user access permissions and roles.
Data Protection
- Data Classification: Classifying data based on its sensitivity and implementing appropriate security controls.
- Encryption Monitoring: Ensuring that data at rest and in transit is encrypted according to best practices.
- Data Loss Prevention (DLP): Implementing measures to prevent unauthorized data exfiltration.
Visibility-as-Code: This component quickly supports new cloud services, preventing security blind spots as organisations adopt new technologies. This service allows security team in defining cloud security policies and configurations using code, rather than relying on manual processes.
Customizable Object-Level Scanning: It enables detailed scanning of objects in S3 buckets for public exposure, sensitive data, and malware detection, allowing users to customize scanning according to their needs.
Our Services
We support CSPM deployment/enablement services for leading Cloud security posture management technologies including.
- Microsoft CSPM
- Palo Alto Prisma Cloud
- WIZ Cloud Security
- Trend Micro Cloud One
- Cloud Native CSPM
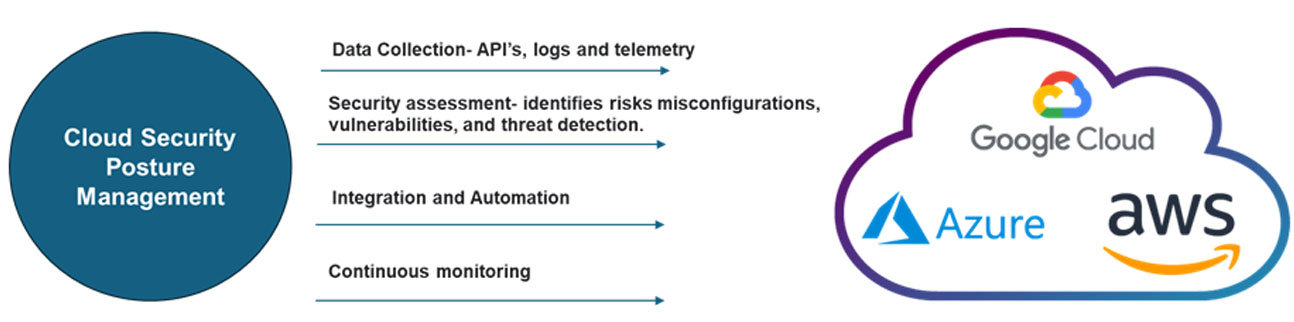
CSPM deployment- Scope of Services
• CSPM Onboarding-Integration with customer cloud Account/Subscription.
• Custom rules / policies.
• Compliance reports advisory.
• Integrate with supported 3rd party tools.
• Project Management and Knowledge transfer.
Contact Us for More Detail
